Today, a large number of users heavily rely on mobile applications to conduct most of their digital tasks. With every passing year, the number of hours people spend on mobile apps every day is increasing gradually, considering the level of technological advancements and digital ease being introduced across all sectors.
Due to this, such mobile apps now hold access to an exponential amount of user data, including sensitive credentials. Such data must be protected from any potential unauthorized access. Therefore, leveraging mobile app security becomes paramount! Your software developers can help you in the process by building secure applications, but you still need to know how it works.
So, this article will help you understand what mobile app security is and how it works or can be implemented for your brand platform.
Understanding Mobile App Security
In simple words, mobile app security is a process that involves the use of multiple security procedures or technologies for protecting mobile applications from data theft or cyber attacks. Some important measures, like authorization and encryption, are used across diverse devices or operating systems to encourage mobile app security.
For software developers, mobile app security stands as a critical approach they ensure high-value applications are built to be safe from fraudsters. Threats like reverse engineering, keylogging, malicious attempts, and tampering are certain interferences that can compromise data on your mobile devices. Adequate security measures can prevent that!
Therefore, right from the development stage, it becomes important for you to create a sophisticated mobile application security plan, backed with technology solutions like:
- Secure communication protocols
- Authentication & authorization
- Secure code practices
- Data encryption
- App permissions
- Secure storage
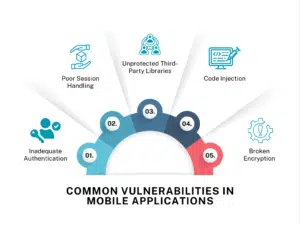
Common Vulnerabilities in Mobile Applications
With the rising threats to mobile applications, it becomes increasingly necessary to implement thorough testing and the adoption of security measures. Here are some of the vulnerabilities that have inclined almost all developers to practice secure measures to build their mobile apps:
1. Inadequate Authentication:
Mobile apps implementing soft authentication mechanisms, lacking hardcoding of passwords or Multi-Factor methods, will eventually lead to security breaches. Thus, users’ accounts as well as their critical information might be at risk.
2. Poor Session Handling:
Inefficient session management strategies can trigger fixation attacks or session hijacking. In such cases, attackers will pose as a validated user to conduct unauthorized activities.
3. Unprotected Third-Party Libraries:
Mobile apps built with unprotected third-party components or libraries might lack the necessary security features and might not receive timely updates. Therefore, such libraries are susceptible to security vulnerabilities.
4. Code Injection:
There are common exploits, such as SQL injection vulnerability, RCE, or XXE injection, capable of enabling attackers to inject compromising code into the backend of your mobile app. Thus, it will tamper with the overall system inputs and breach the app data.
5. Broken Encryption:
When you have broken or weak encryption algorithms embedded in your mobile app, it will be at risk of losing confidential user or admin information. Implementation shortcomings or inadequate key management strategies are often the common reasons.
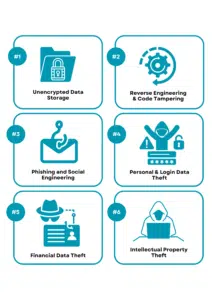
Top Security Risks that Can Compromise Mobile App Security
Here are some of the top security concerns that can compromise the security of your mobile app and give hackers complete control over the stored data:
1. Unencrypted Data Storage:
Storing critical details such as tokens, private info, and passwords without proper encryption will encourage hackers to gain unauthorized access and misuse them.
2. Reverse Engineering & Code Tampering:
Cyber attackers might work their way to delete the source code of your mobile app or modify its behavior. For the worse, they can also attempt to reverse engineer the app, resulting in exposing it to critical vulnerabilities or extracting its data.
Hackers use phishing or social engineering tactics to trick users into giving up sensitive information or performing certain actions that can lead to financial or data loss.
4. Personal & Login Data Theft
Attackers tend to steal the sensitive personal or login credentials of users or clients, which might cause them financial or social loss, leading your brand to face unwanted criticism.
5. Financial Data Theft
Digital banking is now conducted through mobile apps and consists of critical financial details of users, including debit or credit card credentials. Poor security encourages hackers to get hold of such data and take control of users’ devices to process transactions.
6. Intellectual Property Theft
Patents, copyrights, and other intellectual property rights can also fall into malicious hands. For instance, your mobile app is built on a specific set of code, and hackers can steal it to create a copy of it, deceiving users into downloading the fake version over your real software.
Implementing Mobile App Security Testing to the Rescue!
The first step in ensuring the security of your mobile application is to test it at the development stage. This is the process where your mobile app will undergo several test cases to determine what type of threats or malicious attempts it can deal with!
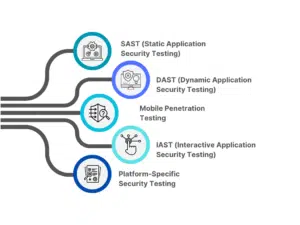
Such an effort will help you determine the security vulnerabilities or weaknesses of your mobile app, giving you a chance to fix them before it is deployed. Here are some of the ways the mobile application security testing is conducted:
-
SAST (Static Application Security Testing):
When conducting SAST, your mobile app will be tested for the bytecode, binaries, or application code. There are automated tools for the needful that can determine any potential code imperfections, such as hardcoded credentials, API misuse, data validation issues, or vulnerable coding styles.
-
DAST (Dynamic Application Security Testing):
As the name suggests, DAST is meant to test the mobile app in its running state. The purpose is to detect any potential security loopholes from the users’ perspective while the app is in its complete potential. It is the test case where automated scanning is conducted to look for unethical usage of user input, session management issues, authentication failures, and other such issues.
-
Mobile Penetration Testing:
Penetration testing is of utmost priority to establish authority and security for your mobile application. The purpose of this test is to put your mobile app under trial for dealing with real-life security challenges or errors. It is also referred to as ethical hacking! An expert will conduct mobile penetration testing by using methods such as payload injections, traffic interception, network mapping, and others.
-
IAST (Interactive Application Security Testing):
With IAST, you will be testing your mobile app on a combination of both DAST and SAST models. This testcase will run at the time of app execution, and will be monitored for its response to potential threats. In this testing approach, a virtual version of your mobile app will be put to action and will be marked for any run-time vulnerabilities.
-
Platform-Specific Security Testing:
People preferably use either Android or iOS devices to download and engage with your mobile application. Therefore, it is important to implement platform-specific testing to review the security permissions, exploits, vulnerabilities, rules, and encryption mechanisms. You might have to incorporate different security practices for Android and iOS platforms separately.
Added Practices to Strongly Implement Mobile App Security
In order to make mobile app security work, here are some of the added practices that you ought to strongly implement alongside thoroughly testing them before deployment:
1. Secured Coding Efforts:
Your developers must strictly adhere to safe coding practices throughout the SDLC to get rid of potential vulnerabilities. This way, your app will be safe from injection attacks, buffer overflows, or input validation issues.
2. Proper Encryption of Data:
Data encryption is paramount for mobile app security by using strong and dependable algorithms. Moreover, the data at rest or stored on devices is the most vulnerable and needs special encryption strategies.
3. Protected Backend Infrastructure:
You need to prioritize setting up secure servers, APIs, and a database with firewalls, access controls, IDS, and encryption. Implement secure API design approaches such as rate limiting, data validation, and authentication to better serve the purpose.
4. Input Validation:
Leverage input validation to prevent attacks like cross-site scripting, command injection, and SQL injection. You can practice using input validation libraries and parameterized queries to do the needful.
5. Ongoing Security Testing:
Mobile app security testing shouldn’t be a one-time thing! There must be a periodic schedule to conduct ongoing system security checks. Under this, you must conduct DAST, SAST, IAST, penetration testing, and automated scans to detect potential flaws.
How Can Simpalm Help You with Mobile App Security?
At Simpalm, we don’t just build powerful and high-performance mobile apps, but also guarantee absolute security and stability for them in the long run. Our team is trained, skilled, and educated to align your mobile app security measures with the latest and most common threats lurking in the minds of cybercriminals.
We have the right tools and resources to not just implement the right test cases for your mobile app, but also to establish a robust security infrastructure for it. As part of our ongoing support and maintenance services, we will be conducting timely security audits and will be upgrading the associated tools or measures, keeping your app protected for users in the long run.
Our team will drive focus on securing your app as well as its back-end infrastructure, ensuring both users as well as your brand operations stay unaffected due to digital threats. Let our experts pave the path and provide you with end-to-end secured mobile app development solutions!
Conclusion
In order to protect your brand reputation and scale it in the long run, you ought to give your users something beyond quality services or products. You ought to give them the assurance that their data is protected on your platform!
Therefore, prioritizing mobile app security will not just help protect the critical data of users but will also boost your brand integrity. Secure authentication techniques, data encryption, risk management, and other such measures are to be necessarily implemented for dealing with emerging cyber threats.
In this quest to address the security threat of your mobile app, Simpalm can be of your utmost assistance. For more information on our secure mobile app development solutions, reach out to us!

 App Development
App Development Web Engineering
Web Engineering AI Services
AI Services Health / Fitness
Health / Fitness Education
Education Social
Social Nonprofit
Nonprofit Fintech
Fintech Logistics
Logistics Government
Government HR Software
HR Software About Simpalm
About Simpalm Our News
Our News Client Testimonials
Client Testimonials Careers
Careers Awards
Awards Resources
Resources Information
Information